Cyber Security Course in Visakhapatnam | Of course. Here is a full, detailed explanation of a Cyber Security Course, covering its importance, domains, career paths, and what to expect from a comprehensive program.
What is a Cyber Security Course?
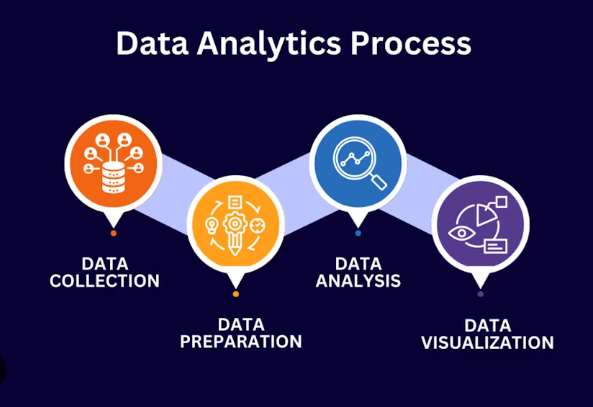
Cyber Security Course in Visakhapatnam | A Cyber Security course is a structured training program designed to teach the principles, tools, and techniques used to protect computer systems, networks, programs, and data from digital attacks, damage, or unauthorized access. The goal is to ensure the Confidentiality, Integrity, and Availability (CIA Triad) of information.
Who is this Course For?
- IT Professionals: Network administrators, system administrators, and help desk technicians looking to specialize in security.
- Career Changers: Individuals from other fields seeking to enter the high-demand cybersecurity industry.
- Students & Recent Graduates: Top Cyber Security Course in Visakhapatnam | Computer science or IT students wanting to build a security-focused career.
- Software Developers: Engineers who need to write secure code and understand application vulnerabilities.
- Compliance & Risk Officers: Professionals responsible for ensuring organizational adherence to security standards.
- Anyone Concerned with Privacy: Individuals wanting to protect their personal data and understand digital threats.
Core Components & Syllabus (Full Details)
A comprehensive cybersecurity course is structured around key knowledge domains that map to real-world security functions. Best Cyber Security Course in Visakhapatnam | The curriculum typically progresses from foundational concepts to specialized skills.
Part 1: Security Foundations & Core Concepts
- The CIA Triad: Confidentiality, Integrity, and Availability as the cornerstone of security.
- Threat Landscape: Understanding attackers, their motives (hacktivists, nation-states, cybercriminals), and common attack vectors.
- Authentication, Authorization, and Accounting (AAA): Principles of access control (e.g., Multi-Factor Authentication, Role-Based Access Control).
- Network Security Fundamentals:
- TCP/IP model and common protocols.
- Firewalls, Intrusion Detection/Prevention Systems (IDS/IPS), and VPNs.
- Network segmentation and defense-in-depth.

Part 2: Threats & Vulnerabilities
- Malware Analysis: Understanding viruses, worms, trojans, ransomware, and spyware.
- Social Engineering: Techniques like phishing, spear phishing, and pretexting.
- Web Application Attacks: Deep dive into the OWASP Top 10, including:
- Injection attacks (SQLi, Command Injection)
- Cross-Site Scripting (XSS)
- Broken Authentication
- Security Misconfigurations
- Network-based Attacks: Denial-of-Service (DoS), Man-in-the-Middle (MitM), and DNS spoofing.
Part 3: Defensive Security (Blue Team)
This focuses on protecting and defending an organization’s infrastructure.
- Security Operations Center (SOC) Skills:
- SIEM (Security Information and Event Management): Using tools like Splunk or ArcSight to collect, monitor, and analyze log data.
- Incident Response: The lifecycle of preparing for, detecting, containing, eradicating, and recovering from a security incident.
- Digital Forensics: Preserving and analyzing digital evidence from computers, networks, and mobile devices.
- Vulnerability Management: Scanning for, identifying, prioritizing, and remediating vulnerabilities.
Part 4: Offensive Security (Red Team)
This involves thinking like an attacker to find weaknesses before malicious actors do.
- Ethical Hacking & Penetration Testing: Legal methodologies for testing defenses.
- Reconnaissance: Passive and active information gathering.
- Scanning & Enumeration: Discovering networks, systems, and services.
- Gaining Access: Exploiting vulnerabilities to gain a foothold.
- Post-Exploitation: Maintaining access and covering tracks.
- Tools of the Trade: Hands-on experience with Kali Linux, Metasploit, Burp Suite, Nmap, and Wireshark.
Part 5: Governance, Risk, and Compliance (GRC)
- Risk Management: Identifying, assessing, and mitigating risks to an acceptable level.
- Security Frameworks & Standards: Implementing controls based on NIST CSF, ISO 27001, or CIS Controls.
- Laws & Regulations: Understanding GDPR, HIPAA, PCI-DSS, and other compliance requirements.

Key Features & Teaching Methodology
- Hands-On Labs: The most critical component. Using virtual labs (e.g., Hack The Box, TryHackMe, RangeForce) to practice skills in a safe, legal environment.
- Capture The Flag (CTF) Competitions: Practical exercises that simulate real-world security challenges.
- Case Studies: Analyzing real-world breaches to understand what went wrong and how to prevent it.
- Tool Proficiency: Gaining experience with industry-standard security tools.
Common Certifications Aligned with Courses
- Entry-Level:
- CompTIA Security+: The industry-standard foundational certification.
- ISC² Certified in Cybersecurity (CC): A new entry-point for the field.
- Intermediate:
- CEH (Certified Ethical Hacker): Focuses on offensive security tools and techniques.
- CISSP (Certified Information Systems Security Professional): A management-level certification for experienced professionals.
- Advanced/Specialized:
- OSCP (Offensive Security Certified Professional): A highly respected, hands-on penetration testing certification.
- GCIH (GIAC Certified Incident Handler): Focuses on incident response and forensics.
Benefits of Learning Cyber Security
- Extremely High Demand: A massive global skills gap means millions of unfilled jobs.
- Competitive Salaries: Cybersecurity professionals command high salaries due to demand.
- Diverse Career Paths: Opportunities in technical, managerial, and consulting roles.
- Intellectual Challenge: Constantly evolving threats require continuous learning and problem-solving.
- Making a Difference: Protecting critical infrastructure, personal data, and national security.
Challenges & Considerations
- Constant Learning: The threat landscape changes daily; you must be committed to lifelong learning.
- High Responsibility & Stress: The consequences of failure can be significant (data breaches, financial loss).
- Broad & Deep Knowledge Required: Requires understanding of networking, operating systems, coding, and human psychology.
- Ethical Implications: The skills learned carry significant ethical responsibility.
What to Look for in a Good Cyber Security Course
- Hands-On, Lab-Centric Curriculum: Theory is useless without practice.
- Industry-Experienced Instructors: Teachers should have real-world security experience.
- Updated Content: The course must cover current threats and modern tools, not just outdated concepts.
- Certification Preparation: Alignment with respected certifications adds significant value.
- Active Learning Community: Access to forums or study groups for collaboration and support.

Career Paths After a Cyber Security Course
- SOC Analyst
- Vulnerability Analyst / Penetration Tester
- Security Engineer
- Incident Responder
- Security Consultant
- Forensic Analyst
- Chief Information Security Officer (CISO)
Conclusion
A Cyber Security course is an essential investment for anyone looking to build a future-proof career in technology. It provides the foundational knowledge and practical skills to defend against the ever-growing spectrum of cyber threats. In our increasingly digital world, the work of cybersecurity professionals is critical to the functioning of businesses, governments, and society as a whole, making it one of the most impactful and rewarding fields of the 21st century.
Who’d be a CISO nowadays? Expected to set and oversee information security strategy, and potentially take the fall should a breach occur. Top Cyber Security Course in Visakhapatnam| You need eyes in the back of your network, trust in your team and the ability to influence the board with sound business arguments, not horror stories.
The world’s first CISO is widely acknowledged as Steve Katz, who was hired by Citigroup in 1995 after it came under attack from a hacker trying to steal $10m by gaming the international transfer funds system. The breach was spotted by members of the Citigroup team who noticed anomalies on transactional printouts and rang the alarm. The fact that this issue was captured by employees rather than being flagged by the system led Katz to state: “It shows you the importance of people within the overall information security process. They are your greatest risk, and your greatest asset.”
“It shows you the importance of people within the overall information security process. They are your greatest risk, and your greatest asset.”
Steve Katz
In this article, the second in our Cyber Security Series, we’ll look at the most common types of cyber crime and the actions we can take as a result. Let’s begin by being clear on one thing:
Cyber crime sits in the hands of people, not PCs
The first point in considering cyber crime is that there is always a person, or people, behind any criminal action. Fortunately, we’re not yet in a position where devices have decided of their own free will to empty the bank accounts of innocent citizens or steal organisational data – what would a laptop want with £1,500 or the passport number of Bill Evans from Solihull?
Because we know that it’s other human beings behind criminal activity, we have a distinct advantage over computers – the ability to think in a way that only humans do. Best Cyber Security Course in Visakhapatnam | And whilst we may not personally understand what drives someone to become a cyber criminal, we can be clear on why someone wants to attack our organisation. Broadly speaking, these reasons will fall into one of the following categories:

Childs Play
Life for teenagers has changed a lot in the last twenty years. Whereas previously you might have got your kicks by graffitiing a shop front or setting off a fire extinguisher, you can now wreak havoc with a cheap drone and some basic coding skills. Cyber Security Course in Visakhapatnam | The expansion of IoT-enabled devices is leading to a trend in breaches that might perhaps fall under the category of ‘mischief’ such as hijacking office lighting.
Lessons Learned
Where there’s an IP address, there’s a way. Organisations need to think not just about core infrastructure, but every single connected device. Gartner predicts that by 2020, more than 25% of identified enterprise attacks will involve IoT.
An axe to grind
We all have the occasional bad day at work, but some people take their grievances to extremes. The well-publicised Morrisons data breach in 2014, which compromised the details of 100,000 employees, and cost the company £2m to put right, was put down to the actions of just one disgruntled employee. Andrew Skelton was sentenced to eight years in prison but that wasn’t the end of the story. In December 2017, the High Court ruled that Morrisons was ‘vicariously liable’ for the breach, paving the way for a compensation claim filed by over 5,000 staff and highlighting even greater need for employers to think about who has access to their data.
Lessons Learned
Data security is not just ‘an IT issue’. In this instance, HR comes into play as it is believed that Skelton’s motivation was the result of a disciplinary procedure. Questions have since been raised about whether it is appropriate for employees facing disciplinary action to continue to have access to confidential data. This article offers some sound advice on how companies can seek to minimise the risk of employees causing, or falling victim to, a breach.
Financial gain
Why go to the risk and trouble of robbing a bank or conning people on their doorstep when you can steal hundreds of thousands of pounds from the comfort of your own laptop? As we make our homes and buildings safer, criminals are quick to seek out weak spots beyond our four walls – and as it stands, there’s still plenty to exploit. A court sentenced British cyber criminal Grant West to more than 10 years in prison after finding him guilty of defrauding individuals and selling information that had been stolen from organisations including Asda, Ladbrokes, Barclays and BA.
Lesson Learned
Corporate data doesn’t just sit within HQ. Some of the information stolen was via reward systems – BA’s data was stolen via Avios. This means that to adequately protect the information held on your customers, your third party partners and suppliers must hold the same high standards as you.

A secondary element in this case was the use of phishing. West sent emails purporting to be from Just Eat, offering a reward in return for card details. Just because these emails were consumer in nature, it doesn’t mean that they weren’t viewed or responded to on corporate devices. Adequate employee training and controls to capture phishing emails will minimise the effectiveness of this kind of attack.
Organised crime
Europol’s Serious and Organised Crime Threat Assessment (SOCTA) report details the rapid expansion of ‘traditional’ organised crime groups into online activities, resulting in the creation of Crime as a Service or ‘CaaS’. CaaS allows entry-level cyber criminals to carry out attacks at a scale disproportionate to their technical capability. In 2016, an international criminal infrastructure platform known as ‘Avalanche’ was finally dismantled after four years of co-operation between law enforcement agencies, investigators and prosecutors from 30 countries. To give an idea of the scale of the Avalanche platform, its dismantling resulted in the seizing and blocking of over 800,000 domains. The precise cost of the damage caused by the platform is unknown, but conservatively estimated to be in the hundreds of millions of Euros.
Lesson Learned
Cyber crime is serious business and it’s growing. We need to place the same level of importance on protecting our organisations, data and employees at a cyber level as we do on a physical level.
Giving Power to Your People
With so many people potentially out to get your business – how do you know who the ‘Good Guys’ are? Going back to Steve Katz’s quote, it’s (almost) everyone in your business. They each have the potential to operate in a manner that greatly reduces the risk of your organisation becoming a victim of cyber crime – and they don’t need to be White Hats to do it. Here’s some quick tips on helping to make sure everyone takes ownership – and the CISO has a fighting chance of successfully implementing their strategy.
Be clear about the impact of a cyber crime
In a worst case scenario, cyber crime results not just in reputational and financial losses, it results in job losses too. Employees need to understand the real-world impact of cyber crime, and the importance of small actions on their part.
Make it real
Helping employees spot the classic signs cyber crime such as phishing emails will have a positive impact on their personal lives. If it helps to give a flavour of the scale, it’s worth knowing that the National Cyber Security Centre (NCSC) Active Cyber Defence programme blocks on average 4.5 million malicious emails a month from reaching users. Cyber security training is not just a ‘corporate initiative’ – it is equipping people to protect themselves from modern crime.
Clearly communicated processes
What should someone do if their device presents a ransomware message? Disconnect from the network? Inform IT security? Clear processes result in decisive action that can minimise the damage of an attack.

Make it an agenda item
If there’s a new threat on the horizon, don’t keep restrict the knowledge to the IT security team. Cyber security should be on everyone’s agenda.
Create an early warning system
Some malware can sit within an organisation for months and it may not choose to surface on the CISO’s desk first. Give employees a clear view of what constitutes unusual or suspicious activity and get them to report it immediately. Put the power in the hands of your people.